The Security Challenge
In today’s digital landscape, cyber threats are growing in both frequency and sophistication, posing significant risks to organisations worldwide. As hybrid work becomes the standard, protecting a distributed workforce and complex IT environments has become a top business priority. Partial or fragmented security measures are no longer sufficient and businesses require comprehensive, integrated solutions that address vulnerabilities across identities, endpoints, data, applications, and infrastructure.
This shift creates a strategic opportunity for Microsoft Partners to position themselves as trusted security advisors. By offering end-to-end security solutions and expert guidance, partners can help customers navigate the complexities of modern security challenges. With Microsoft’s robust security portfolio and a commitment to Zero Trust principles, partners are empowered to deliver holistic services, from implementation to ongoing support, ensuring customers achieve a resilient and adaptive security posture.
Opportunity for Partners:
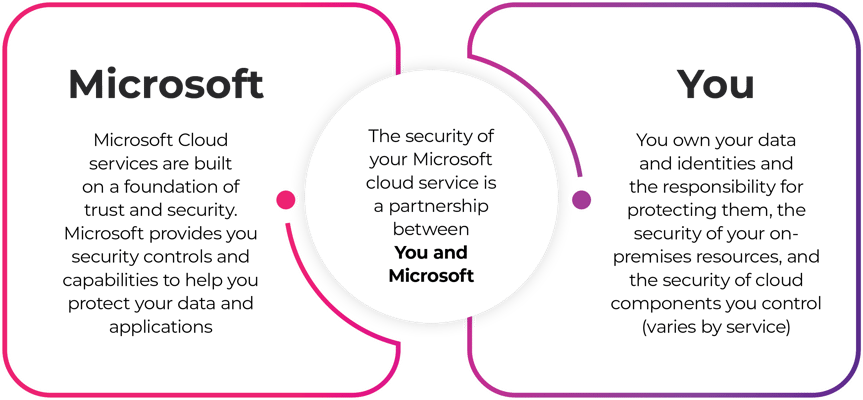
The Shared Responsibility Model
Responsibilities vary based on the type of cloud service being used—whether it’s Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS), or on-premises environments.
Understanding and leveraging this model enables partners to guide customers in optimising security efforts across various cloud environments, aligning each party’s responsibilities for a cohesive security posture.
Microsoft’s Zero Trust security architecture is a comprehensive framework designed to secure modern organisations by assuming that threats come from both outside and inside the network. It operates on the principle of ‘never trust, always verify’.
Using the Microsoft Platform, you can secure identity, endpoints, data, infrastructure, applications and networks – with visibility, automation and orchestration with Zero Trust.
A key priority for Microsoft is making sure every customer and organisation on the planet is secure. Ask Dicker Data about our new Secure Feature Initiative (SFI). It’s about products, best practices and processes that optimise security. Partners can empower the customers and organisations they work with by bringing in a security strategy.”
Daniyel McAvoy, Partner Development Manager, Microsoft
Microsoft Zero Trust Architecture
Your guide to achieving Zero Trust
security with the Microsoft Platform.

Solutions
How Dicker Data helps make Microsoft Security solutions work for you, your practice and your customers:

 Microsoft Purview for Comprehensive Data Protection
Microsoft Purview for Comprehensive Data Protection
Microsoft Purview is positioned as a holistic solution for data governance, data loss prevention, and regulatory compliance. It offers visibility into sensitive data across environments, empowering organisations to enforce policies, manage compliance requirements, and ensure data privacy. Key benefits highlighted by Microsoft include the ability to classify, label, and protect data, helping organisations to manage risks related to data security effectively. This approach is particularly beneficial for industries facing stringent data compliance regulations, offering support for standards like ISO, SOC, and many more.
Microsoft Purview enables comprehensive data protection, helping organisations secure critical information, prevent unauthorised access, and comply with industry regulations. With built-in tools for data classification and tracking, partners can offer customers robust data governance capabilities across hybrid and multi-cloud environments
 End-to-End Protection from Code to Cloud with Microsoft Defender
End-to-End Protection from Code to Cloud with Microsoft Defender
Microsoft Defender for Cloud provides a unified security management system that helps secure workloads across Azure, AWS, and Google Cloud. This solution enables real-time vulnerability assessments, integrates with CI/CD pipelines for DevOps security, and enhances threat protection with AI-based detection and remediation capabilities. Defender for Cloud addresses the critical need for continuous protection across the cloud lifecycle, from infrastructure to runtime, making it ideal for managing cloud-native applications securely.
Microsoft Defender delivers end-to-end security, proactively identifying threats from code development through to cloud deployment. With AI-driven risk assessment and automated remediation, this solution helps organisations protect workloads and maintain strong security postures in complex, multi-cloud environments

 Detection and Response Using Microsoft Sentinel with AI and Machine Learning
Detection and Response Using Microsoft Sentinel with AI and Machine Learning
Microsoft Sentinel is Microsoft's cloud-native SIEM and SOAR solution, designed to provide scalable, intelligent security analytics and threat intelligence. Leveraging the latest advancements in machine learning and AI (including Security Copilot), Sentinel enables real-time threat detection, automated investigation, and accelerated response. This allows organisations to mitigate risks faster and more effectively, while also reducing the burden on security teams through advanced automation and orchestration.
Microsoft Sentinel, powered by AI and machine learning, offers enhanced detection and response capabilities tailored for evolving security landscapes. With built-in automation and threat intelligence, partners can empower their customers to swiftly identify, investigate, and neutralise security threats, improving overall security resilience
Spotlight on Security Programs

Voyager Security & AI Program
The Voyager program, led by Dicker Data's expert cloud solution architects, provides a robust combination of face-to-face workshops and virtual sessions, uniquely designed to go beyond traditional education on demand. It not only delivers in-depth technical training on Microsoft security and AI solutions but also offers valuable insights into sales and marketing strategies, essential for building and expanding a successful security and AI practice. The program includes hands-on simulations and scenario-based learning, equipping partners with the skills and tools to address real-world cybersecurity challenges. With its focus on practical, applied knowledge, Voyager empowers partners to strengthen their security expertise and deliver high-impact solutions to customers.

Solution Designation Specialisation in Security
As part of Dicker Data’s commitment to partner enablement, our experts work closely with partners to achieve Microsoft’s Security Specialisation. This distinction is awarded to those who have proven deep technical acumen and demonstrated success in high-demand security areas within Microsoft Cloud. Going beyond standard designations, this Specialisation signifies a partner’s advanced capabilities and commitment to delivering Microsoft security solutions with excellence.

Security Readiness Assessments
Dicker Data offers access to the Microsoft Solutions Assessment Desk, which provides a comprehensive suite of security readiness assessments. These evaluations are designed to give partners and their customers a holistic view of their cybersecurity posture, identifying gaps and making fact-based recommendations to enhance security frameworks. These assessments support partners in aligning their customers with best practices, preparing them for successful Microsoft technology deployments.
Meet the Security Experts
Dicker Data’s dedicated team of security experts have extensive experience in Microsoft's security offerings and are here to support you deliver comprehensive and secure Microsoft solutions to your customers.
 More Resources
More Resources
Got questions? Get answers
What Microsoft Security Controls should I implement for my customer as a minimum?
What Microsoft Security Controls should I implement for my customer as a minimum?
What Microsoft Security Controls should I implement for my customer as a minimum?
The foundational security controls you implement should be tailored to your customer’s specific needs and compliance obligations. However, Microsoft strongly recommends the following essential security measures as a baseline for all organisations:
- Enable Multifactor Authentication (MFA): Microsoft research shows that enabling MFA blocks over 99.9% of automated attacks. It is a critical first line of defence that all users should have enabled to secure their accounts. Microsoft offers built-in MFA with Azure Active Directory, which integrates seamlessly with M365 and Azure services.
- Adopt the Zero Trust Security Model: Zero Trust is a guiding framework that assumes breaches are inevitable. Following the principle of "never trust, always verify," Microsoft recommends implementing identity verification, device health checks, and strict access controls. Microsoft’s Zero Trust architecture includes tools like Microsoft Entra (for identity and access management), Microsoft Defender for Cloud (for workload protection), and Microsoft Sentinel (for threat intelligence and analytics).
- Enable Conditional Access Policies: Conditional Access in Azure Active Directory allows you to define specific access requirements based on user, location, device state, and app sensitivity, strengthening access control and minimizing risks associated with unauthorized access.
- Implement Endpoint Protection: Microsoft Defender for Endpoint provides advanced threat protection for devices, helping to detect, investigate, and respond to threats on Windows, macOS, iOS, and Android devices. This is essential for protecting endpoints from malware, phishing, and ransomware attacks.
- Use Security Baselines and Compliance Standards: Microsoft offers pre-configured security baselines in Azure and Microsoft 365, aligned with industry standards like CIS, NIST, and ISO, which provide a strong security foundation for compliance.
What license do I need to implement Multifactor Authentication (MFA)?
What license do I need to implement Multifactor Authentication (MFA)?
What license do I need to implement Multifactor Authentication (MFA)?
MFA is considered a security default by Microsoft. Security defaults are free for every customer in Azure Active Directory Premium P1 & P2, and relevant M365 licenses.
What is Zero Trust Architecture?
What is Zero Trust Architecture?
What is Zero Trust Architecture?
Zero Trust Architecture is a modern security framework that assumes no user, device, or network segment should be trusted by default, regardless of whether it is inside or outside the organization’s perimeter. Instead, every access request is verified at each step, ensuring strict security controls across all aspects of the digital environment. Microsoft’s Zero Trust model operates on the core principle of "never trust, always verify."
Here’s how Microsoft implements the Zero Trust principles across its ecosystem:
- Verify Explicitly: Microsoft enforces identity verification at every access point, requiring multifactor authentication (MFA) and leveraging Conditional Access policies in Azure Active Directory. This step ensures that users and devices are verified based on all available signals, including user identity, device health, location, and behaviour patterns.
- Use Least Privileged Access: Access is granted based on the minimum permissions needed to complete a task. Microsoft supports this principle with tools like Microsoft Entra Permissions Management, enabling Role-Based Access Control (RBAC) and Just-in-Time (JIT) access to protect critical resources while limiting exposure.
- Assume Breach: In line with Zero Trust, Microsoft assumes that threats may already exist within the network. Microsoft Defender for Cloud and Microsoft Sentinel provide continuous monitoring, threat detection, and response capabilities. With advanced threat intelligence and AI-driven analytics, these tools help detect suspicious activity and respond rapidly to potential breaches.
- Secure Every Layer: Microsoft Zero Trust encompasses identity, endpoints, applications, data, network, and infrastructure. This comprehensive approach includes:
- Microsoft Defender for end-to-end code to cloud workload protection (CWPP) and posture management (CSPM)
- Microsoft Purview for data protection and compliance powered by AI
- Microsoft Sentinel for centralized SIEM/SOAR capabilities and proactive threat hunting powered by machine learning and AI
By following the Zero Trust model, organisations can create a more resilient security posture that adapts to modern threats, particularly in hybrid and multi-cloud environments.
How can I get help and 1:1 advice on a specific security requirement my customer has?
How can I get help and 1:1 advice on a specific security requirement my customer has?
How can I get help and 1:1 advice on a specific security requirement my customer has?
For personalised assistance on specific security requirements, you can reach out to the Microsoft team at Dicker Data. Our dedicated experts are available to provide comprehensive guidance across product, sales, and technical support, ensuring that your security needs are addressed in line with Microsoft’s latest solutions.
Whether you’re navigating complex compliance requirements, implementing Zero Trust, or enhancing threat detection capabilities, our team is ready to assist with tailored advice and best practices. We offer in-depth expertise on Microsoft security products, including Defender, Purview, Sentinel, and more, to help you architect and deploy the best-fit solution for your customer’s environment.
Contact the Microsoft team at Dicker Data here. Let us help you elevate your security posture with Microsoft’s powerful suite of tools and strategies.
Where is my customer’s data located in Azure?
Where is my customer’s data located in Azure?
Where is my customer’s data located in Azure?
Microsoft Azure has many global regions. You can search the available geographies here.
Are the security recommendations on this page applicable to small environments?
Are the security recommendations on this page applicable to small environments?
Are the security recommendations on this page applicable to small environments?
Yes, Microsoft’s security recommendations are applicable to environments of all sizes. Small and medium businesses (SMBs), like larger enterprises, face growing cybersecurity threats and can benefit from implementing Microsoft’s security best practices. Key controls such as Multi-Factor Authentication (MFA), Zero Trust principles, and endpoint protection are crucial regardless of environment size.
Microsoft provides solutions tailored to SMB needs, such as Microsoft 365 Business Premium, which includes MFA, Conditional Access, and Defender for Business for comprehensive endpoint protection. These solutions offer robust protection that is scalable, cost-effective, and manageable even for smaller IT teams, ensuring that security standards remain high without overwhelming resources.
How should I limit access to Azure subscriptions?
How should I limit access to Azure subscriptions?
How should I limit access to Azure subscriptions?
This can be achieved by using RBAC and following the principle of least privilege. For more information on the type of roles available please explore here.
How can I check if there are any malicious sign-in attempts to my Microsoft Services?
How can I check if there are any malicious sign-in attempts to my Microsoft Services?
How can I check if there are any malicious sign-in attempts to my Microsoft Services?
Azure AD provides a sign-in activity report that can be utilized to check any malicious login attempts to the service. These logs can be further analysed by ingesting the data in log analytics/Microsoft Sentinel.
I want to follow Microsoft security recommendations for various workloads in Azure. Where do I start?
I want to follow Microsoft security recommendations for various workloads in Azure. Where do I start?
I want to follow Microsoft security recommendations for various workloads in Azure. Where do I start?
Various compliance standards such as CIS, and ISO2700 provide detailed instructions around security best practices. Microsoft Azure security benchmark can be used as a reference to implement various security controls for Azure. You can read more here.
Why should a business consider Microsoft Security solution?
Why should a business consider Microsoft Security solution?
Why should a business consider Microsoft Security solution?
1. Unified Security Across Multi-Cloud Environments:
Microsoft Security solutions provide a seamless security framework that spans multi-cloud and hybrid environments. With tools like Microsoft Defender for Cloud, businesses can monitor and protect assets across Azure, AWS, Google Cloud, and on-premises setups, ensuring a consistent security posture across complex IT landscapes.
2. Advanced Threat Intelligence and AI-Powered Defence:
Microsoft leverages a vast global network and applies AI-driven threat intelligence to detect and mitigate threats in real-time. This capability, embedded in tools like Microsoft Sentinel and Defender, allows businesses to proactively identify and respond to sophisticated threats, enhancing the effectiveness of their security operations.
3. Zero Trust Architecture:
Built on Zero Trust principles, Microsoft’s security approach ensures that no entity, whether internal or external, is trusted by default. Every access attempt is verified, providing comprehensive protection across all assets, identities, and endpoints. This model is especially valuable for businesses adapting to distributed work environments and a growing attack surface.
4. End-to-End Coverage with a Broad Security Portfolio:
Microsoft offers a complete suite of security tools that cover every aspect of an organisation's environment, from identities and endpoints to applications, data, and infrastructure. This integration reduces security gaps and simplifies management, making it easier for businesses to maintain a cohesive and comprehensive security strategy.
5. Cost Efficiency and Vendor Consolidation:
Consolidating security under a single vendor like Microsoft reduces complexity and enables cost savings. Microsoft’s unified platform allows organisations to manage multiple security functions without relying on numerous third-party solutions, lowering both licensing costs and operational overhead.
6. Proactive Compliance and Risk Management:
Microsoft provides built-in tools for continuous compliance monitoring and risk management. Features like Secure Score and compliance tracking through Defender for Cloud help businesses maintain alignment with regulatory standards, supporting proactive risk management and giving organisations peace of mind about compliance.
7. Industry Leadership and Innovation:
Microsoft is recognized as a leader in cybersecurity, consistently investing in research and development to tackle evolving cyber threats. This commitment ensures that businesses benefit from cutting-edge protection that adapts to the dynamic cybersecurity landscape, making Microsoft a strong choice for organisations seeking a robust, scalable, and future-ready security solution.
How do I keep my Microsoft tenants secure?
How do I keep my Microsoft tenants secure?
How do I keep my Microsoft tenants secure?
Dicker Data recommends the following actions:
1. Setup MFA. Compromised passwords are one of the most common ways that bad guys can get at your data, your identity, or your money. Using multifactor authentication is one of the easiest ways to make it a lot harder for them.
2. Setup a recovery password. If a hacker gains access to the account and resets the password, you’ll need to follow the password reset steps in order to get back into your account.
In the instance where your tenants are compromised, Microsoft account recovery steps here will help guide you when filling out the account recovery form. Note however that it can be a lengthy process as it's designed to ask questions about your account that only you can answer.
Partner Testimonials
We make Microsoft work for partners. Here’s what they’re saying:
With Dicker Data, we’re in safe hands. They are all about relationships and translating technology into human experiences. They shepherded us through everything and helped us navigate the Microsoft Portal – all of a sudden, the Microsoft tap started to flow.
Stephen Doney, Vendor & Client Relationship Manager, CMTG
We have a truly strategic relationship with Dicker Data. Nothing is too much trouble – it’s a two-way street, and we certainly sense they want to be a part of it. They are ready, willing and able every time. We would not be where we are now without their support.
Ian Nearhos, Head of Strategy, Truis
![]()
Dicker Data helps us navigate the Microsoft Partner Portal and make sure that we leverage all available programs – there’s just too many for us to look after ourselves. We really lean on the Dicker Data relationship there.
James Xuereb, Strategic Partnerships Manager, CNS
![]()
We have regular meetings with our Dicker Data Partner Manager to understand the product roadmap. Knowing the future of Microsoft’s plans, such as Copilot, helped us develop a new product that was close to commercialisation within six weeks. That wouldn’t happen without Dicker Data and Microsoft’s knowledge and expertise.
John Caruso, CEO, Commuserv

Dicker Data’s team of certified professionals combine deep domain knowledge with sharp commercial acumen, making them true partners in our success. Since aligning with Dicker Data, we've witnessed exponential growth in our business and strengthened our relationship with Microsoft. Dicker Data hasn't just been a supplier; they've become an integral part of our business strategy.
Simon Bishop, Director, Cloud Factory

It’s really exciting that we can leverage Dicker Data's experience in Microsoft with the security and Co-Pilot space.
Bernard Moran, Chief Executive Officer, Virtual IT Group

They genuinely feel like they work in partnership with us. It feels like an extension of my own team when we're working together.
Jason Wornham, General Manager, FUJIFILM CodeBlue

There's a reason why they're
Australia's most trusted distributor.
David Crotty, Managing Director, Intergy Consulting

The Dicker Data team's dedication to sharing knowledge and facilitating business development opportunities has been valuable to us. Their expertise, guidance, and proactive approach have enabled us to achieve customer satisfaction, improve operational efficiency, and drive revenue growth. We deeply appreciate the partnership and would highly recommend Dicker Data to other organisations looking to build and develop their Dynamics practice.
Harshana Etampawala – Managing Director, Integral Management Systems

|
|
With Dicker Data, we’re in safe hands. They are all about relationships and translating technology into human experiences. They shepherded us through everything and helped us navigate the Microsoft Portal – all of a sudden, the Microsoft tap started to flow.
|
|
|
We have a truly strategic relationship with Dicker Data. Nothing is too much trouble – it’s a two-way street, and we certainly sense they want to be a part of it. They are ready, willing and able every time. We would not be where we are now without their support.
|
|
|
Dicker Data helps us navigate the Microsoft Partner Portal and make sure that we leverage all available programs – there’s just too many for us to look after ourselves. We really lean on the Dicker Data relationship there.
|
|
|
We have regular meetings with our Dicker Data Partner Manager to understand the product roadmap. Knowing the future of Microsoft’s plans, such as Copilot, helped us develop a new product that was close to commercialisation within six weeks. That wouldn’t happen without Dicker Data and Microsoft’s knowledge and expertise.
|
|
|
It’s really exciting that we can leverage Dicker Data's experience in Microsoft with the security and Co-Pilot space.
|




