Keeping New Zealand Businesses Secure with an Edge
By coupling the most comprehensive range of cybersecurity products with access to the industry's most highly-certified sales and technical experts, Dicker Data has created the leading destination for partners looking to scope, design, and deliver best-practice cybersecurity solutions.
With the threat landscape rapidly evolving, cybersecurity is a fundamental aspect of the modern business landscape — and helping you solve your customers' cybersecurity challenges is what we do best. Lever our knowledge to keep your team focused on winning more business and meeting your customers' needs. Dicker Data is an extension of your team — we're in every opportunity with you, to make sure your solution offering wins every time.
Explore over a dozen vendors with an array of dynamic cybersecurity solutions, including firewalls, cloud security, IoT solutions, and more. Protect yourself and your customers from malware, viruses, ransomware, resource misuse attacks, and other cyber-threats — ensure your safety, security, and success with Dicker Data.
Discover Our Vendors' Leading Cybersecurity Solutions

Manage your endpoints with Citrix, including mobile device management (MDM) and mobile application management (MAM) capabilities.

Deploy Microsoft Defender for Endpoint for a solution that includes automated detection, response and remediation of cyber-attacks.

Protect your network against the latest threats with a comprehensive cybersecurity solution, no matter where users are accessing it from.
Access automated, insightful protection for your users on any device, any application, anywhere with Trend Micro Apex One.
Improve Cyber Resilience to minimise security incidents and unforeseen costs.

Deliver maximum protection with minimal complexity to take the guesswork out of Endpoint Security.

Provide users with one simple platform that reduces data risk, increases visibility, and improves employee data access.

CrowdStrike is now delivering Enterprise Security for the SMB! Protect your endpoints using the latest behavioural and AI based technology backed up by CrowdStrike’s expert Threat Hunters and Managed SOC.

Citrix Endpoint Management
Citrix Endpoint Management empowers you to manage every app, device, and platform on your network from one central location. Your business information stays protected with strict security for identity, devices, apps, data, and networks — while your employees can work how, when, and where they want.

Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is designed to keep modern remote work secure, by providing market-leading next-gen protection against both traditional and the most advanced cyber threats.
Using endpoint behavioural sensors, cloud security analytics, web content filtering, and threat intelligence, Microsoft Defender for Endpoint provides automated detection, response, and fully-automated remediation of even the most sophisticated cyber-attacks.
Defender for Business is now included for small and medium businesses in the M365 Business Premium bundle, at no extra cost.

SonicWall Endpoint Security
Equipped with behaviour-based malware protection, advanced threat hunting, and visibility into application vulnerabilities, SonicWall Capture Client delivers modern endpoint protection with centralised control.
As the work from home movement continues to grow, the opportunities for endpoint vulnerabilities expand with it. Protect your network with Capture Client and Content Filtering, the comprehensive cybersecurity solution for devices on the go.
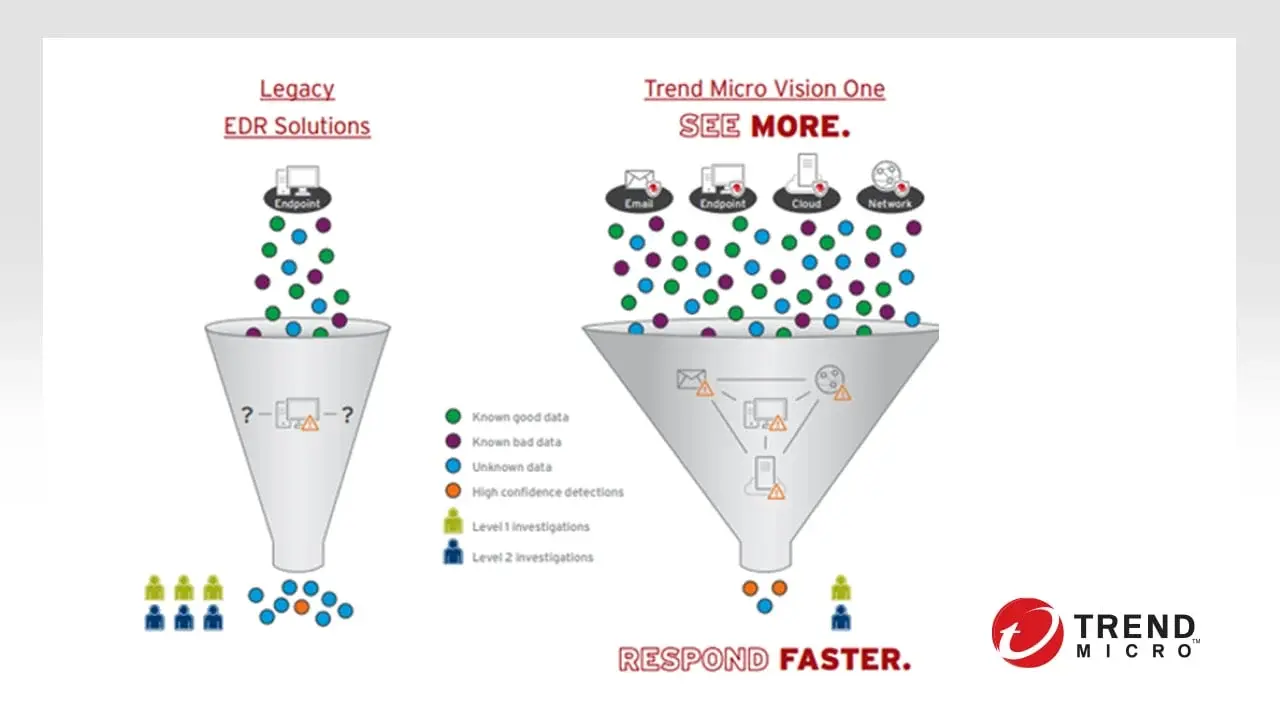
Trend Micro Apex One
You can have it all with Trend Micro Apex One endpoint security. Defend against malware and ransomware attacks with advanced threat protection, and use extended detection and response (XDR) to hunt threats across email, endpoints, servers, clouds, and networks. Timely virtual patching will protect newly-exposed vulnerabilities until official patches are deployable. And in the unlikely event that anything does get through, Apex One has your back with ransomware rollback to restore your data.
Trend Micro Apex One is available as a service, so deployment is flexible and it's always up to date with the latest protection for your system. On-premises and hybrid options are also available.

Endpoint Security with OpenText Cybersecurity
OpenText Cybersecurity Endpoint is a comprehensive, automatic backup solution for all your endpoint devices and the data that resides on them. It simplifies the administrative tasks associated with deploying protection across an entire organisation, no matter the size, distribution or sophistication of the environment.
Highly automated OpenText Cybersecurity Security Awareness Training delivers measurable results with the minimum of effort through, continuous education programs that combine microlearning, phishing simulations with effectiveness measurement and executive reporting, specialty compliance courses, courseware and phishing templates.

Endpoint Security with WatchGuard
WatchGuard’s Endpoint Security platform delivers maximum protection with minimal complexity to take the guesswork out of endpoint security. WatchGuard's user-centric security products and services offer advanced EPP and EDR approaches with a full suite of security and operations tools for protecting people, devices, and the networks they connect to from malicious websites, malware, spam, and other targeted attacks.
Commvault Endpoint Security
Dicker Data and Commvault work closely with partners and their end users to empower a mobile workforce, so users are protected across all environments.
Commvault Complete™ Backup & Recovery for Endpoint provides users with one simple platform that reduces data risk, increases visibility, and improves employee data access. It's available on-prem, via public or hybrid cloud, or on a SaaS model.

CrowdStrike Enterprise Security
CrowdStrike delivers unparalleled visibility and automation by including native SIEM and SOAR solutions with their End Point protection. Add 2 way integrations, available with hundreds of other security solutions, and you can expand your view and response capabilities far beyond the endpoint.

Oversee a remote or hybrid workforce with confidence against the latest, most threatening security risks.

Deliver advanced network security inside your data center, providing application visibility and protection from cyber threats.

Get the edge on evolving threats with advanced protection for networks of all sizes, from small businesses through large data centres.
Discover the art of prevention, detection, and response while eliminating your network security blind spots.
The first DNS protection service to truly combine privacy and security for cyber resilience.

With WatchGuard get full visibility and make timely and effective decisions about your Network Security anywhere, anytime.

Rely on Commvault's essential, simple-to-implement processes for effective network management and security.

CrowdStrike provides comprehensive visibility and response capability to combat known and unknown malicious Network Threats. In additional CrowdStrike offers a centralised Firewall Management tool to easily deploy custom controls and configurations across your organisation.

Citrix Network Security
Citrix secure access solutions make it easier than ever to support hybrid work, by placing security controls close to end users. They simplify security management by unifying all your secure access needs into one stack, with one intuitive dashboard for full visibility and control. The result is a hassle-free, comprehensive secure access experience that makes sure you stay ahead of threats.

Nutanix Network Security
Nutanix Flow delivers advanced network security inside the data center, providing application visibility and protection from the spread of cyber threats like ransomware.
Nutanix Flow offers native network micro-segmentation, which simplifies and automates the application of granular network policy between virtual machines. Networks and applications can easily be segmented using software-defined policy, without any additional hardware or complex network configurations. The result is user-centric protection and a great level of control, without the management overhead.

SonicWall Network Security
Cybercrime is on the rise, but you can protect yourself with SonicWall's award-winning next-generation firewalls and advanced threat protection technology.
Along with full system emulation and virtual sandboxing, SonicWall uses patented Real-Time Deep Memory Inspection techniques to force malware to reveal itself before it can infect your network. Block unknown threats at the gateway, no matter the size of your network — SonicWall has firewalls suitable for everything from small businesses through to large, distributed data centres.
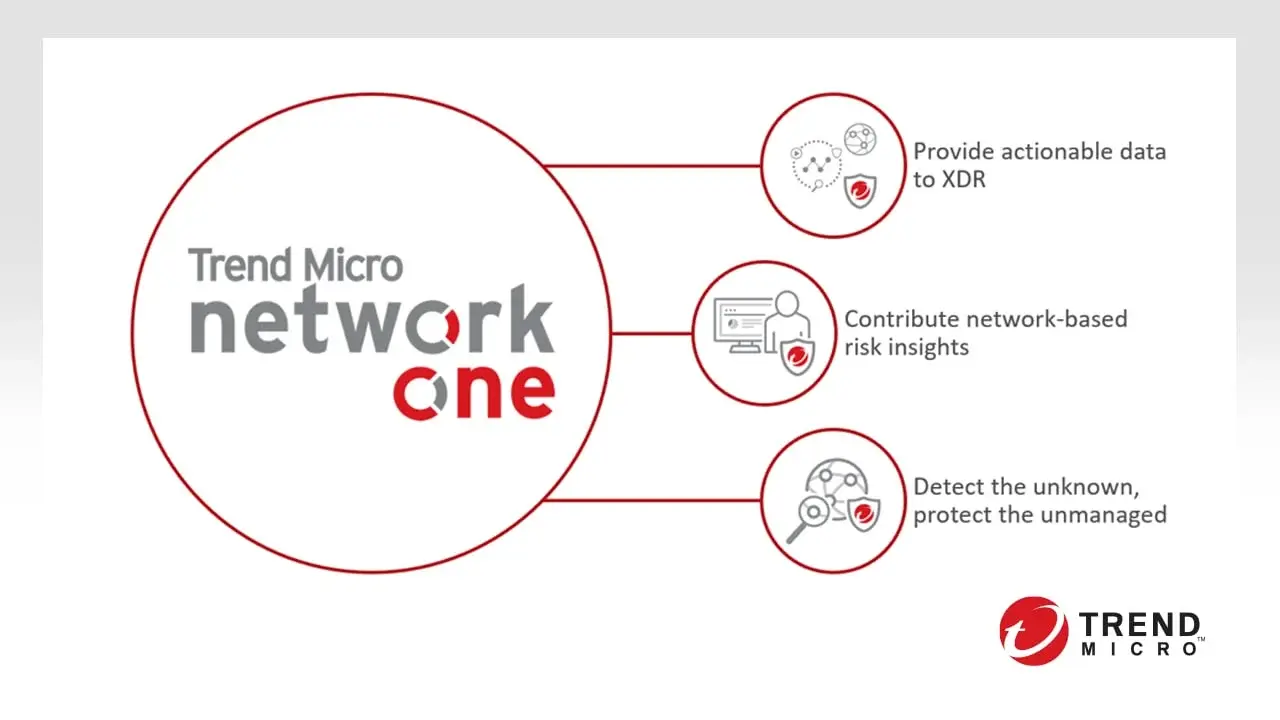
Trend Micro Network One
Eliminate blind spots on your network and protect against all sorts of zero-day threats, including malware, suspicious URLs, exploits, and not-yet-exploited vulnerabilities. With Trend Micro Network One, your organisation can monitor traffic moving inbound, outbound, and laterally across your network — and react and respond to malicious activity and suspicious behaviour at the network layer and beyond.
To find out more click here.

Opentext Cybersecurity DNS Protection
Opentext Cybersecurity DNS Protection automatically filters DNS and DoH requests to malicious and dangerous domains, blocking 88% of known malware before it can hit your network or endpoints, provides private DNS resolvers in Google Cloud™ to stop internet usage request surveillance by bad actors, or those mining data for profit, provides network, IP address, and user policy management over bandwidth and unproductive or noncompliant internet access, using 80 URL categories, uses the most timely, accurate and reliable DNS filtering intelligence backed by the Webroot BrightCloud® Web Classification Service.
WatchGuard Network Security
WatchGuard Firebox is a comprehensive advanced network security platform that puts IT security professionals back in charge of their networks with widely deployable, enterprise-grade security and threat visibility tools suitable for any organisation, regardless of budget, size, or complexity.
Commvault Network Security
Security-conscious organizations trust Commvault for their multi-layered, zero-trust approach to data protection. They offer robust ransomware detection, protection, and recovery across virtual, physical, cloud, and SaaS workloads. Policies such as air gap isolation, immutable backups, restricted write and delete privileges, and network segmentation are easy to implement in Commvault.
Commvault follows the authentication, authorisation, and accounting (AAA) security framework for intelligently controlling access to computer resources, enforcing policies, and auditing usage.
CrowdStrike Network Security
Utilising their light-weight sensor, CrowdStrike is able to monitor HTTP/HTTPS traffic for malicious Patterns, Domains and IPs addresses. By leveraging one of the largest Cyber Security install bases in the industry CrowdStrike is able to maintain an extensive and up to date Threat database containing over 300M IOCs (Indicators of Compromise) and growing. These same IOCs are used to detect, investigate, and respond to cyber threats across your cloud, endpoint, and identity workloads. Not just limited to monitoring and detection, CrowdStrike can also take automated, at scale responses to protect your environment from Network based threats. Automatically blocking Domains, IP Addresses and File Hashes. With 3rd party integrations response actions can even be taken “off-network” at Firewalls, Mail Filters, ZTNA providers and more to shift and extend the security defences away you’re your critical assets.

Support more efficient work environments and multi-cloud deployments with the Citrix suite of cloud security solutions.

Deploy posture management and threat detection services that strengthen security across the cloud, hybrid and other platforms.

Provide native platform hardening, security auditing, reporting and protection from network threats with Nutanix Enterprise Cloud.
Leverage a security services platform for organisations building a hybrid cloud infrastructure with Trend Micro Cloud One.

Detect and respond to global threats with Trustwave's strong partner networks and extensive cybersecurity experience.
Powerful AI/ML backed insights available via modular services.

Ensure secure, reliable data protection for cloud solutions — including applications, DBaaS, VMs, and more.

Discover SecurID and Netwitness cloud security solutions from RSA, and reduce the risk of cybercrime on your business.

Stop cloud threats in real-time with advanced runtime protection using both agent and agentless sensors. These unified Falcon sensors provide deep visibility, detection, and response across the entire cloud-native stack, covering all workloads, containers, and Kubernetes environments.

Citrix Cloud Security
Citrix offers a variety of cloud security solutions that enable safer use of, and access to, applications of all types. Support more efficient remote work environments and multi-cloud deployments with Citrix Secure Private Access and Citrix Workspace.
Citrix Secure Private Access provides adaptive access and authentication for cloud users and their devices, while supporting zero trust network access (ZTNA). Citrix Workspace builds upon single sign-on (SSO) and multi-factor authentication (MFA) to make it easier for cloud users to work remotely.

Microsoft Defender for Cloud
Microsoft Defender for Cloud is a Cloud Access Security Broker (CSAB). Cloud native and fully integrated, Defender for Cloud provides posture management and threat detection services that strengthen security across workloads in the cloud, hybrid, and other platforms.
Defender for Cloud combines continuous risk assessment, security recommendations, and defence and data security policies. The result is a robust CSAB including access and session controls for any cloud application, threat detection from cloud apps, data loss prevention, data encryption, and data governance.

Nutanix Cloud Security
Nutanix delivers the simplicity and agility of public cloud alongside the performance, security, and control of private cloud. Whether on-prem or hybrid, build the exact cloud you want, with unified management and operations, one-click simplicity, intelligent automation, and always-on availability. The Nutanix Enterprise Cloud provides native platform hardening, security auditing and reporting, and protection from network threats.
Trend Micro Cloud One
Cloud service and SaaS providers work hard to deliver a secure environment, but you can't rely on their efforts alone to protect you against ransomware attacks and other security vulnerabilities. You need additional protection for the data and workloads you put in the cloud.
Trend Micro Deep Security uses a blend of cross-generational threat defence techniques to secure your hybrid cloud infrastructure, and integrates with cloud platforms like AWS and Azure. Additionally, Trend Micro Cloud App Security uses advanced techniques such as sandbox malware analysis to protect file sharing applications like Microsoft Office 365, Dropbox, Google Drive, and more. Access Trend Micro's solutions delivered as a service, and protect your assets in the cloud with a security solution delivered in the cloud. To find out more click here.

Trustwave Cloud Security
Trustwave is a global security leader in stopping cyberthreats in the hybrid multi-cloud world. With more than 2,000 security-focused professionals operating on behalf of 5,000 clients in 96 countries, Trustwave has over 25 years of experience helping organisations detect and respond to global threats.
Dicker Data is proud to offer leading cybersecurity solutions from Trustwave to our strong partner networks, including: SpiderLabs Threat Hunters, who provide human-led vulnerability and penetration testing; MailMarshal Cloud, an email security layer that can be applied to Microsoft Exchange, Google Suite, and more; and Security Colony, a subscription knowledge base compiling years of cyberthreat research across hundreds of companies.

Webroot BrightCloud Threat Intelligence Services
Carbonite Cloud-to-Cloud Backup (previously known as CloudAlly) is the ideal SaaS application backup solution, to back up the data for your Microsoft 365, Google Workspace, Sharepoint, Box, Dropbox, and Salesforce applications. Boasting central management, granular restore, rapid recovery, and flexible retention options, this cloud backup solution is perfect for all businesses utilising cloud apps.

Commvault Cloud Security Solutions
With Dicker Data and Commvault, learn how you can protect and secure cloud data. Commvault solutions allow for users to migrate data to, from, and between clouds with ease. Manage data between diverse cloud and on-premises environments, automate disaster recovery, and securely store data in the cloud with Metallic Cloud Storage service.

SecurID & Netwitness Cloud Security
The workplace is evolving, and the shift to cloud means looser perimeters and more security challenges. SecurID, an RSA business, has everything you need for identity and access management in the cloud. SecurID offers easily available, flexible multi-factor authentication (MFA) tokens that balance convenience and security.
NetWitness Cloud SIEM, also from RSA, offers world-class system information and event management without the traditional IT requirements. With NetWitness Cloud SIEM, you will have access to high-performance log management, retention, and analytics services in a simplified cloud form. Maximise your resources and minimise administrative overhead with this quick-to-deploy, easy-to-operate solution.

CrowdStrike Falcon Cloud Security
CrowdStrike Falcon Cloud Security integrates every aspect of cloud security - CWP, CSPM, CIEM, CDR, AI-SPM, and ASPM - into a unified console delivering deep visibility, detection and real-time response across the entire cloud-native stack. Enhancing visibility and business context into cloud applications by automatically mapping and identifying each microservice, database, API, and dependency. This enables customers to assess the business criticality of every attack surface, vulnerability, and threat.
Accelerate mean time to respond by 89% with leading cloud detection and response (CDR) that unifies elite 24/7 managed services and world-class threat intelligence with the industry’s most complete cloud security platform to stop breaches

Gain the visibility you need from security analytics to protect your digital workspace. Proactively detect and resolve security threats with real-time security analytics.

Build your hybrid cloud architecture on a robust software foundation with Nutanix critical infrastructure security solutions.
Offer Best of Breed industrial control systems cybersecurity, and ensure your network's reliability and safety from cyberattacks.

Deliver 24x7 Managed Detection and Response services, powered by the Trustwave Fusion platform and SpiderLabs threat intelligence.
Keep critical systems online all the time with OpenText Cybersecurity.
Employ skilled security resources to manage, detect, investigate, and respond to evolving modern threats.

CrowdStrike delivers a unified XIoT security strategy for Critical Infrastructure that addresses visibility, threat prevention, and identity protection under one framework, to protect your most critical assets, maintain continuous uptime, and stay ahead of evolving adversarial tactics.

Citrix Critical Infrastructure Security
To guard sensitive data, you need to keep assets and employees secure in real time. Citrix Analytics for Security gives you proactive security protection without complicating your employee experience.
Gain the visibility you need from security analytics to protect your digital workspace. Proactively detect and resolve security threats with real-time security analytics. To guard sensitive data, you need to keep assets and employees secure in real time. Citrix Analytics for Security gives you proactive security protection without complicating your employee experience.

Nutanix Critical Infrastructure Security
The robust foundation for Nutanix's critical infrastructure security solution is their proprietary Acropolis operating system (AOS). This hardened platform allows for powerful and secure hyperconverged infrastructure (HCI), letting you leverage hybrid cloud architecture at any scale. With powerful integrated virtualisation overseen by your choice of leading hypervisors and the Nutanix Prism infrastructure control panel, Nutanix promises flexible, resilient, and reliable protection for your enterprise cloud.
Build fast, efficient, secure, and scalable datacentres on a strong foundation, and make virtual machine setup and administration as easy as checking your mail. Accelerate your digital transformation with Nutanix and Dicker Data.

TXOne Networks
Infrastructure isn't just digital — it's also physical. Take a practical approach to cybersecurity in the operations technology sector. Protect your industrial control systems to ensure their reliability and safety from cyberattacks, using OT-native TXOne from Trend Micro.
Fulfil your workforce, workplace, and workload security needs and protect your assets, devices, and people using a zero-trust methodology designed for industrial environments. To find out more click here.

Trustwave Critical Infrastructure Security
Trustwave is a global security leader in stopping cyberthreats in the hybrid multi-cloud world. With more than 2,000 security-focused professionals operating on behalf of 5,000 clients in 96 countries, Trustwave has over 25 years of experience helping organisations detect and respond to global threats.
Penetration Testing
End-to-end pen testing allowing you to proactively identify known and unknown threats, vulnerabilities and cybersecurity risks to your people, process and technology.

OpenText Cybersecurity Availability
OpenText Cybersecurity enables organizations to maintain the highest availability of their Windows® and Linux servers by preventing downtime and data loss. Continuous, byte-level replication maintains a secondary copy without taxing the primary system or network bandwidth.

BlackBerry Cybersecurity Critical Infrastructure
BlackBerry Cybersecurity solutions are simple to use, fast and extremely reliable. With one of the most configurable crisis management systems available. Activate your full emergency response in less than 10 minutes. Get real-time visibility into your personal safety, while centralising all communications by operating from one dashboard. BlackBerry AtHoc helps businesses prepare for, respond to, and recover from disruptive events.

CrowdStrike XIoT Assets
XIoT assets power critical operations but are notoriously hard to monitor and protect. CrowdStrike secures them all with one unified platform, delivering real-time visibility, AI-powered threat prevention, and identity protection built for the XIoT age. The CrowdStrike Falcon agent, validated by leading ICS vendors like Rockwell Automation and Siemens, protects XIoT assets from tailored malware and ransomware designed to shut down operations without impacting operations.

Deploy comprehensive, industry best practice security with Microsoft's comprehensive application security solution.

Visualise, secure, and segment your hybrid multi-cloud and prevent data loss with Nutanix Flow application-level security.
Easily implement detection and prevention for modern applications and APIs using Trend Micro Cloud One application security.

Manage digital risk and provide secure access to cloud applications with SecurID and Netwitness from RSA.

CrowdStrike Falcon Cloud Security application security posture management (ASPM) gives teams a way to identify, assess and prioritise their top application security risks based on what’s running in production right now.

Microsoft Application Security
Microsoft Application Security is a comprehensive solution set including Windows Defender App Control (WDAC) and Code Integrity Signing, Attack Surface Reduction, Application Protection Policies and Defender for Cloud. Across managed and unmanaged devices alike, it’s never been so easy to deploy industry best practice security while aligning to global and regional industry security standards such as Essential 8.
Nutanix Application Security
Nutanix Flow addresses many private cloud security challenges, including at the application level. Visualise and discover apps and their network connectivity. Segment apps and virtual networks without hardware or complex networking. Secure applications, prevent data loss and support compliance goals.
With Dicker Data and Nutanix Flow, gain insight into the communication and vulnerabilities of all your apps, and learn how you can best secure your hybrid multi-cloud.
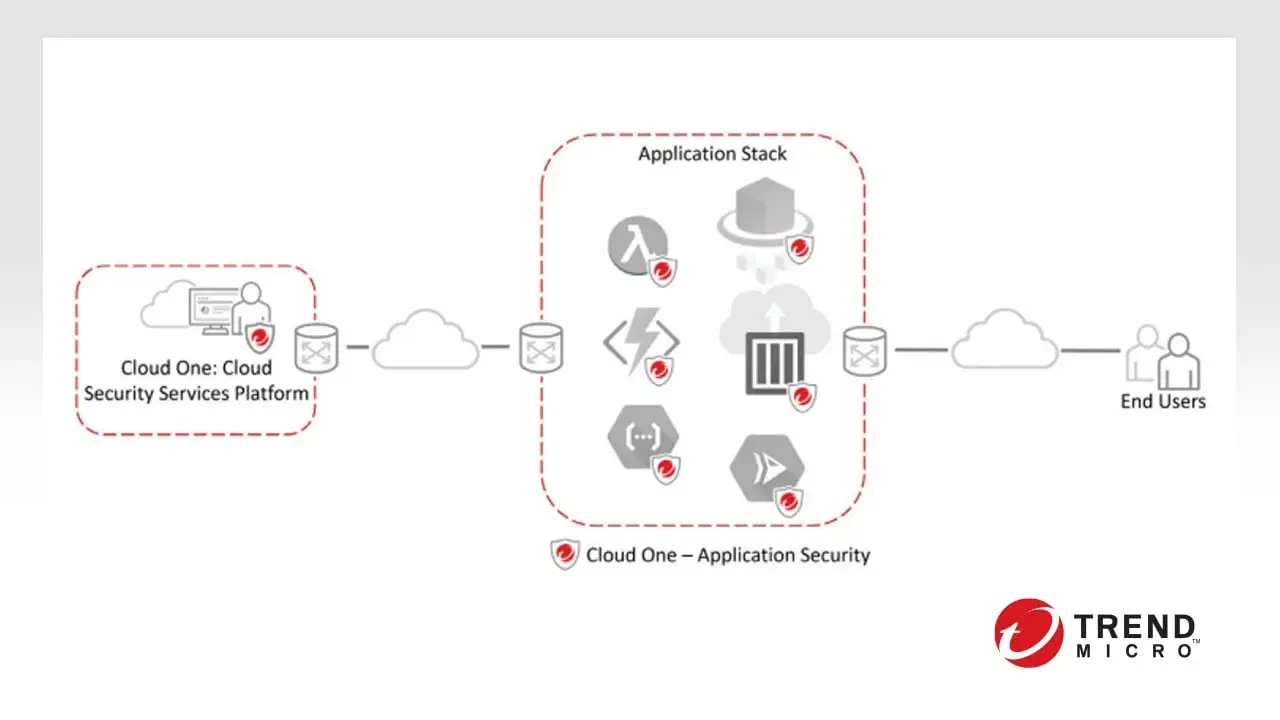
Trend Micro Cloud One™ Application Security
Build secure applications with Trend Micro Cloud One Application Security. Minimise your risks during the design and deployment process, by protecting against sophisticated hacks from the inside. Discover threats and vulnerabilities, remediate them at speed, protect your users and server code — and spend more time delighting your customers instead of performing security maintenance.
To find out more click here.

SecurID & Netwitness Application Security
RSA offers application security solutions through SecurID and NetWitness.
When users need to connect with data and applications across a multitude of platforms, SecurID delivers the don’t-think-twice-about-it secure access that makes everything effortless and worry-free for IT security teams. SecurID provides a broad array of flexible authentication options for access to data and applications.
NetWitness is an information and event management product that gathers all the information from application log files and detects anomalies. Rapidly detect and respond to threats with NetWitness.

CrowdStrike Falcon Cloud Security
See your security landscape through the lens of business priorities. Know the real-world implications of each threat, helping you understand where to focus your defense. Automatically identify critical data flows in your deployed applications. Spotlight and protect data that could be exploited - PII, PCI, and PHI, we’ve got it covered. See a detailed bill of materials for every software dependency, proprietary, or open-source library that exists within your cloud applications or microservices. Automate incident management workflows across security, DevOps, and engineering teams with integrations for Jira, Azure DevOps, and ServiceNow.

Maintain data security as well as legal and regulatory compliance throughout the lifecycle of your data.
Opentext Cybersecurity’s data protection and migration solutions provide large organizations and small to medium-sized businesses uninterrupted access to critical business data.

Ensure data availability with a single backup and recovery interface, accessible from wherever your data lives.

A modern approach to effortlessly stop data theft. The industry’s only unified platform for data protection built on a unified agent and single console.

CrowdStrike Data Protection delivers complete, real-time data protection without complexity. Achieve rapid, frictionless deployment at scale with a single platform across endpoints and cloud environments. Get instant visibility into data flows with near-zero configurations.

Microsoft Data Management
Microsoft 365 Compliance is a cloud-native hosted service offering comprehensive compliance and data governance solutions to help your organisation manage sensitive data and the risks it poses throughout its lifecycle. With extensive global, regional, and country-specific compliance templates augmented by machine learning and artificial intelligence, Microsoft 365 Compliance provides a full end-to-end data management solution.

Opentext Cybersecurity Backup & Data Protection for Businesses
Achieve end-to-end backup and data protection with the Carbonite product suite.
OpenText Cybersecurity Cloud-to-Cloud Backup helps businesses quickly recover their SaaS data and reduce the impact of data loss to become more cyber resilient. OpenText Cybersecurity Backup for Microsoft 365 offers comprehensive backup for the entire Microsoft 365 suite of productivity apps. OpenText Cybersecurity Server is a secure, all-in-one server backup and recovery solution for physical, virtual, and legacy systems. OpenText Cybersecurity Recover reduces the risk of unplanned downtime by securely replicating critical systems to the cloud, providing an up-to-date copy for immediate failover.

Commvault Backup & Recovery
Commvault Backup and Recovery offers one secure data backup solution for your entire environment, no matter where your data lives. With simple, comprehensive archiving and scalable cloud data mobility, you can easily recover files, apps, databases, containers, and more from a single user interface.
For enterprise-grade, industry-leading data protection without the complexity, there's Commvault Metallic SaaS. Choosing the backup-as-a-service model offers you easy deployments, automatic upgrades, no hardware costs, and a predictable subscription model — eliminating the stress of maintenance and infrastructure expenses. Metallic options include: VM and Kubernetes Backup, File & Object backup, Database Backup, and Metallic for Salesforce, Office 365 and Endpoints.

CrowdStrike
Eliminate blind spots immediately, get instant visibility into data flows, with near-zero configurations, to understand both the known and unknown egresses. Stay compliant and ensure security control with minimal configuration to detect and prevent sensitive PCI, PHI, PII data leakage.

CrowdStrike Data Protection
CrowdStrike delivers the industry’s only unified platform for data protection built on a unified sensor and single console providing continuous visibility into data at rest and in motion across endpoints and cloud environments. Helping you and your clients gain an understanding of both known and unknown egresses in real time, maximizing protection while minimizing complexity. Capability to detect unauthorized access, anomalies, and insider risks in both stored and transmitted data before they escalate.

Combining cutting-edge, AI-powered cybersecurity technology with the industry’s top security analysts, Falcon Complete Next-Gen MDR expands the scope of visibility beyond native endpoint, identity and cloud security telemetry.

CrowdStrike
With third-party data from CrowdStrike Falcon® Next-Gen SIEM, Falcon Complete Next-Gen MDR stops breaches across the entire attack surface 24/7 with unmatched speed and precision.
Key benefits of Falcon Complete Next-Gen MDR:
Access world-class security expertise to outpace the adversary and eradicate today’s toughest threats. Stop breaches across the attack surface with 24/7 expert-led protection. Get outcomes, not homework, with full-cycle remediation delivered by the Falcon Complete Next-Gen MDR team.
Frequently Asked Cybersecurity Questions
How do I build a cybersecurity practice with Dicker Data?
Firstly, you will need to be a Dicker Data partner, if you are not yet a partner you can sign up here.
Our dedicated, in-house security specialist team comprising of Product Managers, Business Development Managers, Sales Manager, Technical Specialists, Presales Specialists, and more are some of the most certified in the New Zealand Distribution landscape. Contact our local team and we can walk through your requirements together.
Can I purchase cybersecurity solutions, products and licenses through Dicker Data?
Yes, however you will need to be a registered Dicker Data partner. If you are not yet a partner you can sign up here.
Most solutions and products can be viewed on our transactional portal, log in here. Otherwise, please contact our cybersecurity team to discuss your solution requirements.
Note: In some instances, you might also need to be a registered vendor partner in order to purchase specific solutions. If you need assistance with becoming a vendor partner please contact our local team.
How do I implement Zero Trust in my business?
Zero Trust can be defined in many ways and have just as many models as outlined by different vendors and cybersecurity organisations. The overarching Zero Trust model has one axiom: “Trust No One.” A good security posture should be planned and implemented with this in mind, because attacks and threats can transpire from inside the network as well as from the outside.
Therefore, no device or user should be given default access to any resource, and every access should be protected with a reputable authentication solution and security protocols — whether accessing from within the network perimeter, or from the outside.
Read more: 5 Steps to Implementing a Zero Trust Security Strategy
Why are GDPR and NDB important to my customers?
Collecting data such as business and personal information has always been a commonplace practice for a range of companies. While it was assumed that businesses should lock it down and keep it safe as part of standard operating procedure, unless there was gross negligence or a huge attack it has not been front of mind for many companies, in particular SMBs.
GDPR (General Data Protection Regulation) and NDB (Notifiable Data Breach) are frameworks for industry to make sure that all necessary data is protected, and reinforced via fines or censure if infringements have been proven. While GDPR focuses on personal data of European citizens, it is still enforceable to any Australian business that has an establishment, offers goods and services or monitors the behaviour of individuals in the EU. It should also be noted that the Australian Privacy Act 1988 shares many common requirements with GDPR.
What are the benefits of a layered security model?
A layered security model takes into account that there is not a single system / appliance / software that will be able to stop all the attacks coming into a network. The strategy, therefore, is to have additional systems that can ensure a better coverage.
How to decide what layers should be implemented? Look to an existing layer model like the OSI (Open Systems Interconnection) model, for networking that has 7 layers. Traditional security mechanisms feature in the lower levels (1 - 4), but with the emergence of services and applications, levels 5 - 7 have grown in importance.
Read more: Secure your everything: a guide to layered security
What is cloud compliance and how does it affect me?
A lot of organisations are moving to the cloud, but still have to ensure they are compliant to current laws and regulations. However, having parts of your infrastructure managed by a cloud provider means you need transparency of your platform, systems, usage and users. Without this transparency, you will not be able to identify risks that are born from usage. Unlike on-premises or private clouds, which generally have clearly defined roles (such as datacentre provider, data owners, custodians, etc.), public clouds use a shared responsibility model that requires you to be even more diligent in your efforts for compliance.
Learn more about cloud compliance here.
How do I build a security practice with Dicker Data?
If you are not yet a Dicker Data partner, you can become a partner here.
If so, contact the team and our security specialists will be in touch to walk you through the process.

Get A Cybersecurity Health Check
The Dicker Data Software Security team has collated a list of Cybersecurity Health Assessments alongside our industry awarded security vendors. Let our software team provide you with further information and guidance towards making your cybersecurity solutions a simple, effective and, profitable investment.
Security Health Check
Presales And Complex Solution Architecture
Dicker Data's presales, technical presales and solution architects are the most highly certified in the New Zealand distribution landscape. This means that when you trust us to help solve your customer's business issues, you know you're getting advice from the best in the industry.
Learn More
Learn How To Boost Your MSP Offering
As the rate of digital transformation accelerates, SMB clients are adopting cloud-based IT systems facilitated and secured by trusted MSPs. Whether you are building a security-focused MSP practice or looking for solutions that solve specific customer needs, the team at Dicker Data are on-hand to walk you through our expanding MSP solution portfolio.
Learn moreDelivering Value Added Distribution
Learn how Dicker Data can help your business to scale and compete for larger opportunities through our value-added services. Whether you're just starting your technology business or you're an established organisation, Dicker Data can help you take your business to the next level.
Learn more
Let’s get
Started
Once you get started on your application, you'll need to have the following close by to help you complete the process quicker:
- Your driver’s license
- Your company’s registration information including NZBN
- Full information about your company Directors, including their mobile phone numbers
- Information about the markets your business services
- Trade references for us to contact to verify your business
- A witness to verify your signature
- If trading as Trustee company, you must put the Corporate Trustee Name and NZBN/NZCN and provide a copy of the “Record of Registration” for the Business Name
If you're applying from overseas, please email accounts@dickerdata.co.nz and request an application form.
Fill in the form below to start the
sign-up process with us:
Contact
The Team
If you’re an existing partner, but would like to learn more, please fill in your details and a member of our team will be in touch with you shortly.





