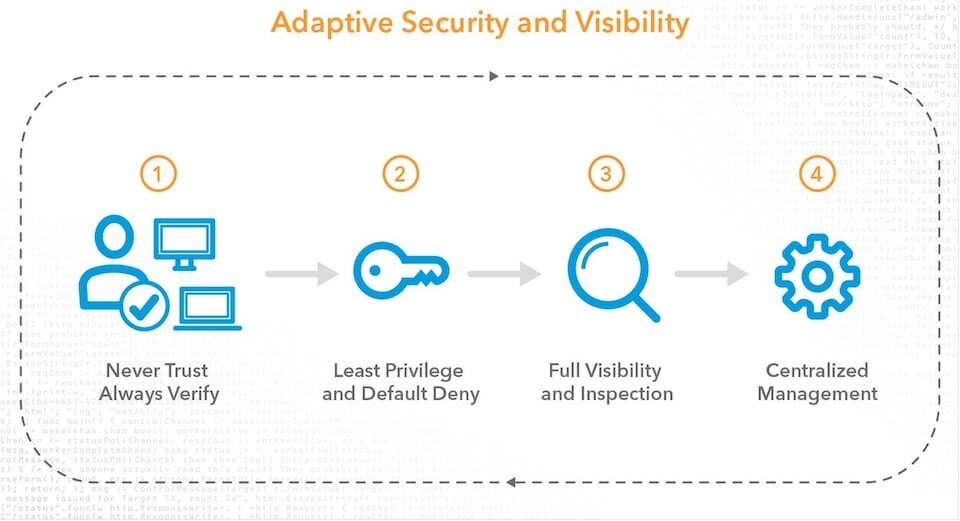
5 Key Steps to Implementing a Zero Trust
 Sam Taylor
Sam Taylor
Sam Taylor
20th April 2021
3 minute read
Microsoft Surface
Networking
Windows 11
Cloud
Uncategorized
Aruba
TechX
AV Solutions
Acronis
Collaboration
Cybersecurity
Events
Hardware
News
Social Media
Software Solutions
TechX 2019
TechX 2022
Trend Micro